Main Menu
Main Menu
News

Data protection and encryption
A Successful Integration
A Successful Integration: RegData Protection Suite (RPS) and Thales CipherTrust We are happy to announce a new integration between two major partners of Kyos: RegData ...
8 May 2024
Data protection and encryption In the news
Read more
In the news
Pentests guide: Protecting your systems from cyber threats
Understanding Pentests: A comprehensive guide In today’s digital landscape, where cyber threats are ever-evolving, safeguarding your organization’s critical assets and sensitive information is paramount. There ...
1 February 2024
In the news
Read more

In the news
KYOS & REGDATA Unveil Strategic Alliance
Dear Madam, Dear Sir, Geneva, 11th of September 2023 – Today, REGDATA, with its innovative in RPS Data Protection & Governance platform, and KYOS, a ...
26 September 2023
In the news
Read more
In the news
nLPD (nFADP) comes into force : obligations and opportunities
The revised Data Protection Act (DPA) has been in force since September 1, 2023, with no transition phase. Its main objective is to protect the ...
11 September 2023
In the news
Read more

In the news
Establish a climate of trust
The term “climate of trust” is much more than just a concept. It’s the glue that forges strong relationships and fosters personal fulfillment within the ...
14 August 2023
In the news
Read more

In the news
Sign your PDFs with an electronic signature
How can you make sure that the PDF is electronically signed while maintaining its authenticity and legal value as when you printed and signed it ...
4 May 2023
In the news
Read more

In the news
Thales creates CDSP out of Vormetric and KeySecure
CDSP out of Vormetric and KeySecure In 2014, when they approached us, Vormetric was already an established company and their Data Security appliance convinced more ...
2 November 2022
In the news
Read more

In the news
Cyber-Safe certified
Have you ever heard of the Cyber-Safe label? The Cyber-Safe label is a guarantee of cybersecurity quality for Swiss SMEs. As an IT service provider ...
31 August 2022
In the news
Read more

In the news
Improve your agility with security
Access your internal resources seamlessly, or when security improves agility The way we work has changed dramatically over the last two years, bringing new challenges ...
22 June 2022
In the news In the news
Read more

In the news
A climate of trust through the culture of feedback
Establishing a climate of trust is like filling a bucket of water with a spoon in the middle of a battlefield; at the slightest jostle, ...
8 June 2022
In the news
Read more

In the news
SecurityScorecard x Kyos – Winetasting Webinar
SecurityScorecard x Kyos – Winetasting Webinar Together with SecurityScorecard we are pleased to organise this event as an online wine tasting webinar. It will take place on ...
27 May 2022
In the news
Read more

In the news
KYOS about the Kaspersky situation
As a Kaspersky Gold partner, we feel that it is time to communicate about the recent situation regarding Kaspersky Antivirus. As you may know, Kaspersky ...
19 April 2022
In the news In the news
Read more

Audit and intrusion tests
We successfully renewed our Crest Membership
Kyos team is proud to announce that we successfully renewed our Crest Membership. This accreditation allows our clients to get CREST Certified penetration testings directly ...
18 October 2021
Audit and intrusion tests Security
Read more

In the news
Get ready, Wi-Fi 6E is coming
What’s going on? Europe has just authorized the exploitation without license of the 6 GHz frequency band (in the 5925-6425 Mhz range) in order to ...
3 August 2021
In the news Wi-Fi and Guest Access
Read more
In the news
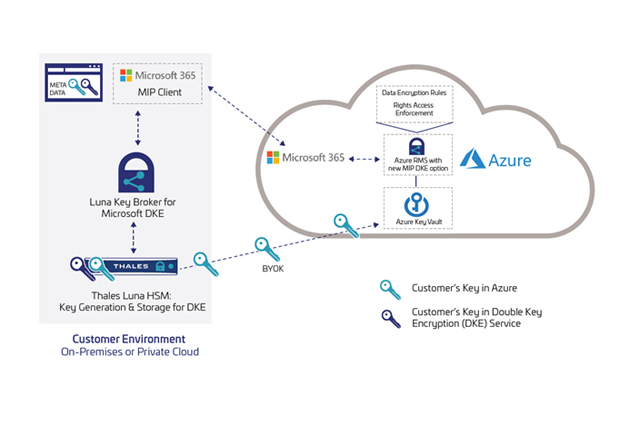
Thales Double Key Encryption (DKE)
Announcing Thales HSM Backed Double Key Encryption for Microsoft Office 365 – The best of both worlds Today’s remote working environment relies heavily on the ...
21 July 2021
In the news
Read more

In the news
Rebranding at KYOS
A new identity for even more expertise With the aim of constantly listening to our employees and our stakeholders in a more global sense, we ...
15 June 2021
In the news In the news
Read more

Data protection and encryption
Thales HSM vs DpoD Cloud
High Assurance Hardware Security Modules Secure your sensitive data and critical applications by storing, protecting and managing your cryptographic keys in Luna Network Hardware Security ...
31 May 2021
Data protection and encryption
Read more

Security
Exchange zero-day Exploit
Whether you are a Kyos customer or not, considering the criticality of this flaw, we offer you a free primary investigation of your Exchange server, ...
9 March 2021
Security
Read more

Security
0-day Vulnerability
On March 2, Microsoft has released an emergency security update for Microsoft Exchange to remediate six vulnerabilities allowing remote code execution, of which 4 can ...
3 March 2021
Security
Read more

Data protection and encryption
What is Double Key Encryption (DKE)?
1. Introduction What is DKE? DKE – or Double Key Encryption– is a new option offered by Microsoft Information Protection (MIP), a cloud-based data classification ...
10 February 2021
Data protection and encryption Security
Read more

Data protection and encryption
Security of data in the cloud
The concept of Cloud has evolved in the last 20 years, and security concerns have grown with it. The first serious effort to provide data ...
1 February 2021
Data protection and encryption Security
Read more
More information on this subject?
We are at your disposal!


